IOCs:
- 80.77.82.40 – wrapsing.gdn – GET /rotation/exoclick – Fake ad server points to RIG EK
- 92.53.105.43 – far.temperedgraces.com – RIG EK
- dxostywsduvmn6ra.onion – Payment domain
- Uses HKLMSoftwareMicrosoftWindowsCurrentVersionRun for persistence
- Ransom notes = !!!!!readme!!!!!.htm
- Filenames aren’t changed and encrypted files aren’t appended with a new extension
- SHA256: b14ffe0bdadfbab0de8b5ef1b5d078a7c500e5f4e164d771163171e1ed170542
File name: RIG EK Flash Exploit.swf - SHA256: 2f51e6819a2dff508dae58abf95b5d381801debe0cd52b88d6ac05ad05531ba9
File name: o32.tmp - SHA256: 6a407e26b35ce7d16be748f5f3839334c9dc6ec5520960f6832b4cf3a61d0e94
File name: 6205c025.exe
Hybrid-Analysis Report - SHA256: 117de6dcfc72be7628d481578ff683aeb7157fbd994377ff7c97ee098e95d2d1
File name: segui.exe.75ecc763c8aeb325547b1f25bb6de17d.exe
Hybrid-Analysis Report
Image of Traffic:
Infection Chain:
The true infection chain for this run was circumvented in that I know a couple decoy sites being used by the HookAds malvertising campaign. Normally a user would be browsing a legitimate website and then be redirected to a decoy site through malvertising. The dummy site contains an iframe that redirects the host to the RIG EK infrastructure.
Here is an image of the iframe found on the decoy site:
The domain wrapsing.gdn resolves to 80.77.82.40. The resolution history for 80.77.82.40 is as follows:
| Domain | First Seen | Last Seen |
| wrapsing.gdn | 3/1/2017 4:03 | 3/1/2017 12:08 |
| chromotor.gdn | 2/28/2017 3:53 | 3/1/2017 8:25 |
| thousales.gdn | 2/28/2017 16:08 | 3/1/2017 2:08 |
| tworotator.info | 12/23/2016 10:46 | 3/1/2017 0:34 |
| threerotator.info | 12/23/2016 22:41 | 3/1/2017 0:19 |
| sapporoads.info | 12/23/2016 4:10 | 2/28/2017 23:39 |
| kagoshimaads.info | 12/1/2016 17:10 | 2/28/2017 22:38 |
| 80.77.82.40 | 11/29/2016 20:25 | 2/28/2017 16:41 |
| antinent.gdn | 2/28/2017 13:46 | 2/28/2017 13:46 |
| austribach.gdn | 2/23/2017 22:46 | 2/28/2017 1:54 |
| mormous.gdn | 2/25/2017 9:54 | 2/28/2017 1:39 |
| sebrisburg.gdn | 2/24/2017 11:04 | 2/28/2017 1:39 |
| goverzia.xyz | 2/23/2017 10:46 | 2/27/2017 15:03 |
| requippped.xyz | 2/22/2017 23:05 | 2/27/2017 10:25 |
| neveraged.gdn | 2/24/2017 22:56 | 2/27/2017 2:11 |
| aristinct.xyz | 2/22/2017 16:10 | 2/26/2017 16:33 |
| patteriod.gdn | 2/25/2017 16:05 | 2/26/2017 8:48 |
| vecheers.xyz | 2/22/2017 4:02 | 2/23/2017 12:32 |
| takamatsuads.info | 12/2/2016 12:45 | 2/21/2017 23:55 |
| onerotator.info | 11/22/2016 13:33 | 2/21/2017 22:56 |
| kumamotoads.info | 1/3/2017 23:17 | 2/21/2017 22:19 |
| kitakiyushuads.info | 12/2/2016 15:05 | 2/14/2017 21:15 |
| adsstation.info | 2/14/2017 20:06 | 2/14/2017 20:06 |
| okayamaads.info | 11/30/2016 15:16 | 12/22/2016 17:43 |
| kanazawaads.info | 12/2/2016 1:44 | 12/22/2016 14:20 |
| sendaiads.info | 12/2/2016 16:05 | 12/2/2016 16:14 |
| naraads.info | 11/30/2016 15:45 | 12/1/2016 1:21 |
| nagoyaads.info | 11/30/2016 6:25 | 11/30/2016 18:39 |
| kobeads.info | 11/30/2016 17:07 | 11/30/2016 17:07 |
| osakaads.info | 11/29/2016 22:40 | 11/30/2016 14:40 |
| fukuokaads.info | 11/30/2016 5:54 | 11/30/2016 14:17 |
| kyotoads.info | 11/29/2016 13:05 | 11/30/2016 4:00 |
| tokyoads.info | 11/29/2016 11:50 | 11/29/2016 11:50 |
The Whois information for 80.77.82.40 is as follows:
| WHOIS Server | whois.ripe.net |
| Registrar | RIPE NCC |
| abuse@ipipe.net (registrant) | |
| Name | HQHost dedicated block (registrant) |
| Organization | hqhost-dedicated-Cl-82 (registrant) |
| Overoptic Systems LTD DBM (admin) | |
| Overoptic Systems LTD Tech (tech) | |
| Street | 13 Freeland Park, Wareham Road (admin, tech) |
| Postal | BH16 6FH Poole (admin, tech) |
| Country | GB (registrant) |
| UNITED KINGDOM (admin) | |
| Phone | 4401202806130 (admin, tech) |
The Whois information for wrapsing.gdn is as follows:
| WHOIS Server | whois.publicdomainregistry.com |
| Registrar | PDR Ltd. d/b/a PublicDomainRegistry.com |
| seoboss@seznam.cz (registrant, admin, billing, tech) | |
| Name | Robert Bulis (registrant, admin, billing, tech) |
| Organization | N/A (registrant, admin, billing, tech) |
| Street | Lysinska 1756/32 |
| City | Praha 12 |
| State | Praha |
| Postal | Postal code 14300 |
| Country | CZ |
| Phone | 420234261846 (registrant, admin, billing, tech) |
| Name Servers | a8332f3a.bitcoin-dns.hosting |
| ad636824.bitcoin-dns.hosting | |
| c358ea2d.bitcoin-dns.hosting | |
| 1a7ea920.bitcoin-dns.hosting |
The email address seoboss@seznam.cz and name Robert Bulis is associated with the following 90 domains:
| Domain | Email Address | Registered |
| germante.gdn | seoboss@seznam.cz | 2/27/2017 |
| dravitalia.gdn | seoboss@seznam.cz | 2/27/2017 |
| slightfall.gdn | seoboss@seznam.cz | 2/27/2017 |
| unexperic.gdn | seoboss@seznam.cz | 2/27/2017 |
| wallther.gdn | seoboss@seznam.cz | 2/27/2017 |
| chromotor.gdn | seoboss@seznam.cz | 2/26/2017 |
| wrapsing.gdn | seoboss@seznam.cz | 2/26/2017 |
| zachael.gdn | seoboss@seznam.cz | 2/26/2017 |
| thousales.gdn | seoboss@seznam.cz | 2/26/2017 |
| sidentitis.gdn | seoboss@seznam.cz | 2/23/2017 |
| concephall.gdn | seoboss@seznam.cz | 2/23/2017 |
| havenhoek.gdn | seoboss@seznam.cz | 2/22/2017 |
| entrary.gdn | seoboss@seznam.cz | 2/22/2017 |
| discussels.gdn | seoboss@seznam.cz | 2/22/2017 |
| austribach.gdn | seoboss@seznam.cz | 2/22/2017 |
| sebrisburg.gdn | seoboss@seznam.cz | 2/22/2017 |
| neveraged.gdn | seoboss@seznam.cz | 2/22/2017 |
| patteriod.gdn | seoboss@seznam.cz | 2/22/2017 |
| rulence.gdn | seoboss@seznam.cz | 2/22/2017 |
| dispanic.gdn | seoboss@seznam.cz | 2/22/2017 |
| mormous.gdn | seoboss@seznam.cz | 2/22/2017 |
| becomple.gdn | seoboss@seznam.cz | 2/22/2017 |
| explosin.gdn | seoboss@seznam.cz | 2/22/2017 |
| aristinct.xyz | seoboss@seznam.cz | 1/25/2017 |
| requippped.xyz | seoboss@seznam.cz | 1/25/2017 |
| vecheers.xyz | seoboss@seznam.cz | 1/24/2017 |
| goverzia.xyz | seoboss@seznam.cz | 1/24/2017 |
| paramework.xyz | seoboss@seznam.cz | 1/18/2017 |
| erodontain.xyz | seoboss@seznam.cz | 1/18/2017 |
| afghanas.xyz | seoboss@seznam.cz | 1/13/2017 |
| matrixial.xyz | seoboss@seznam.cz | 1/13/2017 |
| orderships.xyz | seoboss@seznam.cz | 1/12/2017 |
| babbath.xyz | seoboss@seznam.cz | 1/12/2017 |
| tulsars.xyz | seoboss@seznam.cz | 1/12/2017 |
| misseum.xyz | seoboss@seznam.cz | 1/12/2017 |
| accomaya.xyz | seoboss@seznam.cz | 1/10/2017 |
| maesthe.xyz | seoboss@seznam.cz | 1/10/2017 |
| becombass.xyz | seoboss@seznam.cz | 1/10/2017 |
| fissippi.xyz | seoboss@seznam.cz | 1/10/2017 |
| suggenheim.xyz | seoboss@seznam.cz | 1/10/2017 |
| parenator.xyz | seoboss@seznam.cz | 1/10/2017 |
| variedman.xyz | seoboss@seznam.cz | 1/9/2017 |
| mainful.xyz | seoboss@seznam.cz | 1/9/2017 |
| moransport.xyz | seoboss@seznam.cz | 1/9/2017 |
| prairian.xyz | seoboss@seznam.cz | 1/8/2017 |
| lisborn.xyz | seoboss@seznam.cz | 1/8/2017 |
| nomalist.xyz | seoboss@seznam.cz | 1/8/2017 |
| tructive.xyz | seoboss@seznam.cz | 1/7/2017 |
| summedit.xyz | seoboss@seznam.cz | 1/7/2017 |
| recenturex.xyz | seoboss@seznam.cz | 1/2/2017 |
| encumb.xyz | seoboss@seznam.cz | 1/2/2017 |
| heathbud.xyz | seoboss@seznam.cz | 1/2/2017 |
| harriving.xyz | seoboss@seznam.cz | 1/2/2017 |
| chanicate.xyz | seoboss@seznam.cz | 1/2/2017 |
| oppositive.top | seoboss@seznam.cz | 12/29/2016 |
| philimate.top | seoboss@seznam.cz | 12/29/2016 |
| whimselves.top | seoboss@seznam.cz | 12/29/2016 |
| nebulanti.top | seoboss@seznam.cz | 12/29/2016 |
| doubterror.top | seoboss@seznam.cz | 12/27/2016 |
| immorpha.top | seoboss@seznam.cz | 12/27/2016 |
| maskeletal.top | seoboss@seznam.cz | 12/27/2016 |
| bassacrame.top | seoboss@seznam.cz | 12/27/2016 |
| acireh.top | seoboss@seznam.cz | 12/25/2016 |
| allireva.top | seoboss@seznam.cz | 12/25/2016 |
| evitats.top | seoboss@seznam.cz | 12/25/2016 |
| deyojne.top | seoboss@seznam.cz | 12/25/2016 |
| margoib.top | seoboss@seznam.cz | 12/25/2016 |
| aweeklya.top | seoboss@seznam.cz | 12/24/2016 |
| sustainablea.top | seoboss@seznam.cz | 12/24/2016 |
| identitya.top | seoboss@seznam.cz | 12/24/2016 |
| wholea.top | seoboss@seznam.cz | 12/24/2016 |
| enviroa.top | seoboss@seznam.cz | 12/24/2016 |
| atacano.top | seoboss@seznam.cz | 12/21/2016 |
| craneov.top | seoboss@seznam.cz | 12/21/2016 |
| draegis.top | seoboss@seznam.cz | 12/21/2016 |
| balaurno.top | seoboss@seznam.cz | 12/21/2016 |
| doralda.top | seoboss@seznam.cz | 12/21/2016 |
| findsilver.top | seoboss@seznam.cz | 11/29/2016 |
| staycold.top | seoboss@seznam.cz | 11/29/2016 |
| vertigoads.top | seoboss@seznam.cz | 11/29/2016 |
| startmedia.top | seoboss@seznam.cz | 11/29/2016 |
| cometamedia.top | seoboss@seznam.cz | 11/29/2016 |
| trafficprofit.top | seoboss@seznam.cz | 11/29/2016 |
| mindflash.top | seoboss@seznam.cz | 11/29/2016 |
| mediaqboost.top | seoboss@seznam.cz | 11/29/2016 |
| cozyads.top | seoboss@seznam.cz | 11/29/2016 |
| wildwildmedia.top | seoboss@seznam.cz | 11/29/2016 |
| promohoster.pro | seoboss@seznam.cz | 11/24/2016 |
| alphamedia.pro | seoboss@seznam.cz | 11/24/2016 |
| bestrotation.pro | seoboss@seznam.cz | 11/24/2016 |
All of the domains shown above seem to be using at least one of the following name servers:
- 1a7ea920.bitcoin-dns.hosting
- ad636824.bitcoin-dns.hosting
- a8332f3a.bitcoin-dns.hosting
- c358ea2d.bitcoin-dns.hosting
The majority of these domains are being categorized as malicious. Another thing to note is that during additional runs I saw the site hickenzi.gdn being used, which resolved to 62.138.9.10. It uses the same name servers as the domains resolving to 80.77.82.40 and had the same registrant email address of seoboss@seznam.cz.
Continuing the investigation… The GET request for wrapsing[.]gdn/rotation/exoclick returns RIG’s pre-filter page, otherwise known as firstDetect.js.html. For example, here is a partial image of the pre-filter page code which contains the URL for the landing page:
This causes the POST request for landing page. Below is a partial image of the landing page:
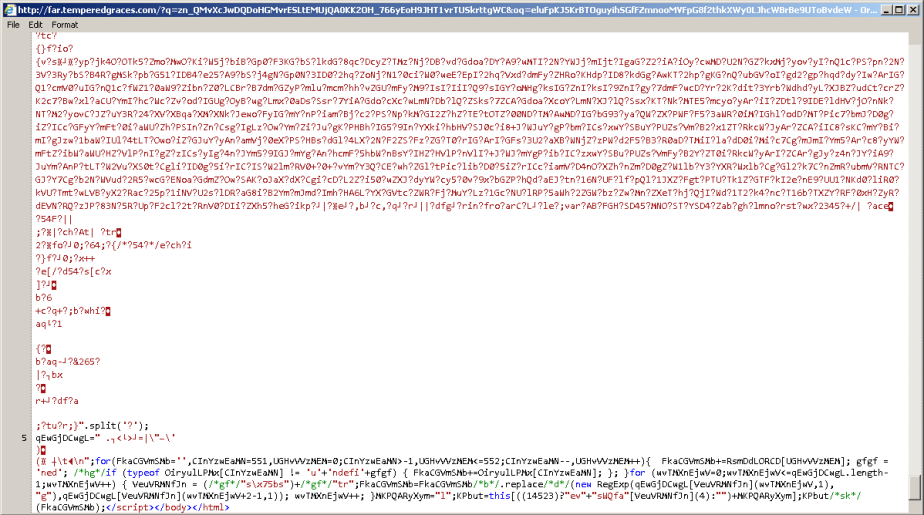
We then see the GET for the Flash exploit:
Followed by the GET for the malware payload:
The script responsible for the GET is contained within o32.tmp, which is dropped into %Temp% and executed:
The payload deletes itself from %Temp% but is copied to %AppData%:
It also creates a registry entry for persistence at HKLMSoftwareMicrosoftWindowsCurrentVersionRun:
Looking at the Hybrid-Analysis report we can see it use the following processes:

We can see it using the command vssadmin.exe delete shadows /all /quiet to delete the Shadow Volume Copies from the system. This means users wont be able to recover their files. User’s should take preventative actions and disable the vvsadmin.exe utility. Read more about this at BleepingComputer.com.
We then see a ransom note pop-up on the Desktop:
I’ve never seen this ransom note before but it was identified as ASN1 ransomware by @PolarToffee at https://twitter.com/PolarToffee/status/837063826436653056.
The infected files weren’t appended with anything and the filenames weren’t altered or obfuscated. I couldn’t find much information on ASN1 but there was a discussion on BleepingComputer.com back on October 21st, 2016, which can be found at the following link: https://www.bleepingcomputer.com/forums/t/630050/asn1-ransomware-key-how-to-use-it/.
We can also see that !!!!!readme!!!!!.htm is dropped in folders containing infected files:
At first glance it doesn’t appear that the media files are infected, however, trying to open the pictures and music didn’t work:
Here is an image of an encrypted file:
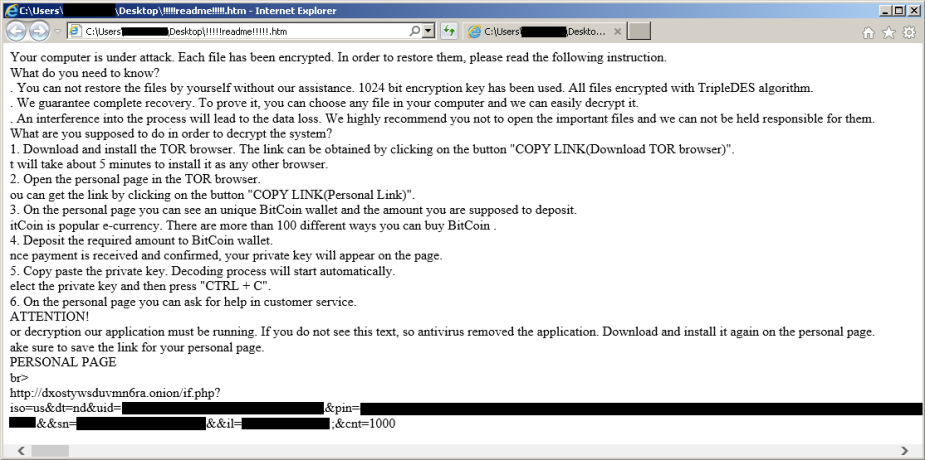
Here is an image !!!!!readme!!!!!.htm:
The URL for the personal page contains the following fields in the query string:
- iso=us
- dt=nd
- uid=32 characters
- pin=3072 characters
- ref=75ecc763c8aeb325547b1f25bb6de17d (segui.exe.75ecc763c8aeb325547b1f25bb6de17d.exe)
- bn=7601.18247.x86fre.win7sp1_gdr.130828-1532 (Build version)
- sn=Windows 7 Home Basic
- il=192.168.XXX.XXX (Internal IP address)
- cnt=289
Installing the Tor browser and following the link for my personal page brought me here:
They are charging 0.5 BTC, which currently equals 614.58 USD. There is a two day count down timer until the price is doubled.
The “Download cryptolocker” link shown on the bottom of the personal page downloaded segui.exe.75ecc763c8aeb325547b1f25bb6de17d.exe. The VT and Hybrid-Analysis report for that file can be found at the beginning of this post.
Clicking on “Chat with support” brings the user to a chat page were they can submit one file for decryption:
After submitting a file it took only a minute for it to be returned fully decrypted. However, nobody responded to my various questions.
The wallet address doesn’t show any payments received:
Until next time!


















[…] 日現在)、その多くが悪意のあるアクティビティにリンクされています。これらにリンクされていることから、この登録者電子メール […]
LikeLike