Originally posted at malwarebreakdown.com
Follow me on Twitter
I received some malspam on 03/22/18 that contained two .doc file attachments. The subject of the email was “Order 2018-048 & 049, Please Confirm”. The attached exploit documents were named similarly to the subject of the email, “PO2018-048.doc” and “PO 2018-049.doc”.
Below is an image of the email:
Both “PO2018-048.doc” and “PO 2018-049.doc” are RTF exploit documents.
An example of one of the files opened is shown below:
Opening either “PO2018-048.doc” or “PO 2018-049.doc” will cause the victim’s host to download the Loki-Bot payload from office.erlivia.ltd:
==================================================
Remote IP Address: 216.200.116.109 (office.erlivia.ltd)
Remote Port: 80
Process Name: EQNEDT32.EXE
Process Path: C:Program FilesMicrosoft OfficeRootVFSProgramFilesCommonX86Microsoft SharedEQUATIONEQNEDT32.EXE
==================================================
The file is downloaded to %TEMP% as RealTEKHD.exe and executed:
RealTEKHD.exe created file %APPDATA%MicrosoftWindowsStart MenuProgramsStartupDropboxInstaller.exe:
DropboxInstaller.exe writes to a start menu file %APPDATA%MicrosoftWindowsStart MenuProgramsStartupDropboxInstaller.Z9yRYh4jbeHJgNMR.lnk:
DropboxInstaller.exe created child process DropboxInstaller.exe, and the child process sends POST requests to the C2 server. The same child process also created B63C85.lck in %APPDATA%E2FBBB and then later deletes the file. The .lck file, which is named after characters 13 through 18 of the Bot GUID, is a lock file (created when decrypting Windows
creds or Keylogging) and is one of the four files that can be found in this hidden folder. The other files are the .exe (copy of the malware used for persistence), .hdb (database of hashes of data that has been ex-filtrated), and a .kdb file (database of keylogger data waiting to be sent to the C2).
The DropboxInstaller.exe child process moves and renames file %APPDATA%MicrosoftWindowsStart MenuProgramsStartupDropboxInstaller.exe to %APPDATA%E2FBBBB63C85.exe.
Hidden folder created in %APPDATA%:
The folder is named after characters 8 through 13 of the Bot GUID. Furthermore, it contains a copy of the malware which has been named after characters 13 through 18 of the Bot GUID.
I ran the sample through another sandbox and the DropboxInstaller.exe child process created a key used for persistence at HKEY_CURRENT_USER. I don’t have a picture of the key to share with you but you can see an example of that at https://www.malware-traffic-analysis.net/2018/03/09/index.html.
More detailed information about the process tree and what changes are made to the file system and registry can be found in the Any.Run and Hybrid-Analysis reports that I’ve linked to in the hash section at the very bottom of this post.
The Bot GUID is created by grabbing the machine GUID from HKLMSOFTWAREMicrosoftCryptographyMachineGuid and generating an MD5 hash from the string. However, only the first 24 characters of the MD5 hash (total of 32 characters) signify the Bot GUID.
Example of Bot GUID:
Machine GUID string (lowercase): 9c3873bd-d616-4eb8-96c2-6aee0ecdf3dd MD5 Hash: 6CD99ACE2FBBB63C852955B3C167AC07 Bot GUID: 6CD99ACE2FBBB63C852955B3
POST to C2:
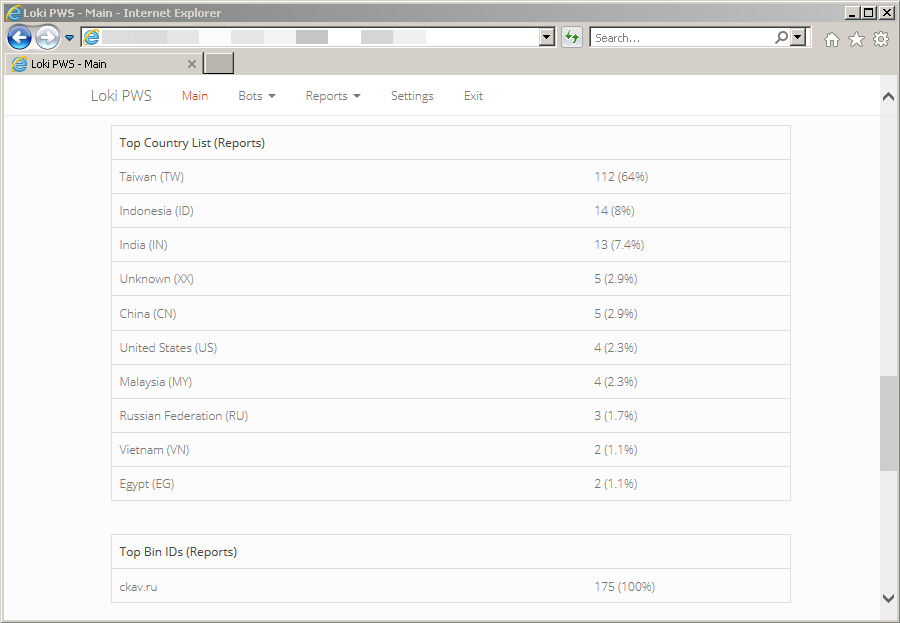
The Loki-Bot sample has a binary ID (Bin ID) of “ckav.ru”. According to what I could find, this binary ID is associated with the Russian hacking forum “fuckav[.]ru”. We also see the victim’s account name, computer name, and Bot GUID.
Loki-Bot C2 panel:
Graphs on data coming in (reports, FTP, HTTP, Other) over the last 24 hours, OS statistics by reports, and OS statistics by Bots:
More statistics:
The Bots section shows the Bot GUID, Bin ID, IP address and country, PC information (computer name, account name, OS, screen resolution, number of reports collected), last time the bot was seen, and action (see commands):
Reports:
Other reports:
HTTP reports:
Example of a report:
Report options:
Commands:
- Download & Run
- Download & Load
- Download & Drop
- Remove Hash DB
- Enable Keylogger
- Shutdown Bot (Only Bot, not PC)
- Update Bot
- Update reconnect intervall
- Uninstall Bot
One thing to note, there are multiple Loki-Bot panels hosted on this server:
cPanel at 89.34.237.212:
Additional Information:
Payloads hosted at *.erlivia.ltd are even being named after the panel locations. For example, VT shows the following URLs hosted at 216.200.116.109:
- 2018-03-26: hxxp://office[.]erlivia[.]ltd/white.123
- 2018-03-20: hxxp://office[.]erlivia[.]ltd/black.123
- 2018-03-20: hxxp://office[.]erlivia[.]ltd/000.123
A full list can be seen HERE.
Subdomains that have a malicious history of their own:
| Subdomains | Resolution History |
| anoti.erlivia.ltd | 89.46.222.212 |
| anotis.erlivia.ltd | 89.46.222.203 and 89.46.222.212 |
| davuchi.erlivia.ltd | 89.46.222.212 |
| lankys.erlivia.ltd | 89.46.222.212 |
| mail.erlivia.ltd | 149.56.100.113 |
| max.erlivia.ltd | 89.46.222.212 |
| maxi.erlivia.ltd | 89.46.222.203, 89.46.222.222, and 89.46.223.221 |
| microsoft.erlivia.ltd | 216.200.116.109 and 185.15.245.88 |
| office.erlivia.ltd | 216.200.116.109 and 185.15.245.88 |
| rov.erlivia.ltd | 89.46.222.203, 89.46.222.222, and 89.46.223.221 |
| windows.erlivia.ltd | 89.46.223.221, 216.200.116.109, and 185.15.245.88 |
A blog post from Proofpoint on 03/23/18 shows maxi.erlivia.ltd hosting a document file that delivered Imminent Monitor RAT: https://www.proofpoint.com/us/threat-insight/post/tax-themed-email-campaigns-steal-credentials-spread-banking-trojans-rats-ransomware
Below is the resolution history for erlivia.ltd:
| Resolution | Location | Network | ASN | First Seen | Last Seen |
| 185.15.245.88 | DE | 185.15.244.0/22 | 24961 | 3/27/2018 | 3/30/2018 |
| 89.46.223.221 | RO | 89.46.223.0/24 | 48874 | 2/9/2018 | 3/27/2018 |
| 89.46.222.222 | RO | 89.46.222.0/24 | 48874 | 2/7/2018 | 2/8/2018 |
| 89.46.222.203 | RO | 89.46.222.0/24 | 48874 | 1/29/2018 | 2/7/2018 |
| 89.46.222.212 | RO | 89.46.222.0/24 | 48874 | 1/11/2018 | 1/27/2018 |
| 89.46.222.187 | RO | 89.46.222.0/24 | 48874 | 1/9/2018 | 1/10/2018 |
| 192.64.119.173 | US | 192.64.119.0/24 | 22612 | 12/5/2017 | 1/8/2018 |
https://www.virustotal.com/en/ip-address/185.15.245.88/information/
https://www.virustotal.com/en/ip-address/89.46.223.221/information/
https://www.virustotal.com/en/ip-address/89.46.222.222/information/
https://www.virustotal.com/en/ip-address/89.46.222.203/information/
https://www.virustotal.com/en/ip-address/89.46.222.212/information/
https://www.virustotal.com/en/ip-address/89.46.222.187/information/
https://www.virustotal.com/en/ip-address/192.64.119.173/information/
VT history shows that some of these panels were once resolving to cliftonltd.ru:
https://www.virustotal.com/en/domain/cliftonltd.ru/information/
SHA256: 4bf2658e0f69865c977cabd24b8dccca38ffc09a17b3367e5f702d2993cf00f7
File name: PO2018-048.doc
Hybrid-Analysis Report
Any.Run Report
SHA256: f9b5535bffd5c0525cb1e59bf79f06d925448b12f106fe1e972473fab4f082fa
File name: PO 2018-049.doc
Hybrid-Analysis Report
Any.Run Report
SHA256: ed5550d3047903d3e09363f90b6d49f519d1484af4e528fd95f1e5f3e5a008b2
File name: RealTEKHD.exe
Hybrid-Analysis Report
Any.Run Report
Network IOCs
- 216.200.116.109 – office.erlivia.ltd – GET /white.123
- 89.34.237.212 – POST /white/fre.php – Loki-Bot C2
- User-Agent String: Mozilla/4.08 (Charon; Inferno)
Additional IOCs
- 89.34.237.212 – POST /black/fre.php
- 89.34.237.212 – POST /000/fre.php
- 89.34.237.212 – POST /annonymous/fre.php
- 89.34.237.212 – POST /pal/fre.php
Samples
The password is “infected”.
References:
- https://isc.sans.edu/forums/diary/3+examples+of+malspam+pushing+LokiBot+malware/23317/
- http://newsroom.trendmicro.com/blog/security-intelligence/cve-2017-11882-exploited-deliver-cracked-version-loki-infostealer
- https://www.sans.org/reading-room/whitepapers/malicious/loki-bot-information-stealer-keylogger-more-37850
- https://r3mrum.wordpress.com/2017/07/13/loki-bot-inside-out/



























you are amazing. i’m in school for secops related stuff rn and i hope to come to your level one day, where i can sandbox an Exploit Kit and use it to figure the whole malwares path and plan out. great job 🙂
LikeLike